|
|
|
|
|
|
| High-speed forensic technology identifies in minutes damage done by targeted cyberattacks |
TOKYO, May 12, 2017 - (JCN Newswire) - Fujitsu announces its high-speed forensic technology(1) to identify the extent of damage targeted cyberattacks cause to an organization's intranet. The new technology, developed by Fujitsu Laboratories Ltd. and to be made available in Japan from June 2017, will accelerate time required to identify damage, from several weeks with conventional technology to several tens of minutes.
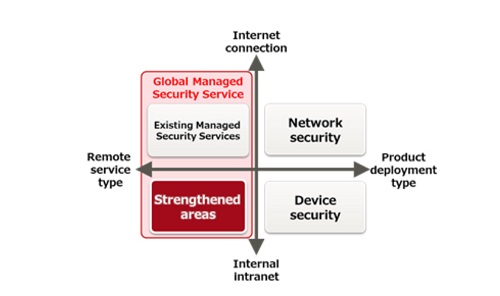 | | Figure 1: Strengthened areas of the Global Managed Security Service |
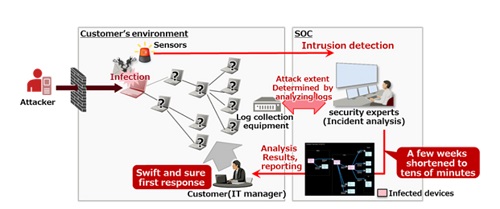 | | Figure 2: New functions utilizing high-speed forensic technology |
Fujitsu will offer the new technology as a function added to its Fujitsu Security Solution Global Managed Security Service, which provides integrated lifecycle support to strengthen security resilience, mitigate risks and minimize damage of cyberattacks.
Fujitsu has also signed an agreement with US-based Dtex Systems to launch solutions in Japan that combine Fujitsu's services with Dtex Systems' advanced user behavior intelligence technology that looks at the ordinary behavior of users at endpoints(2) such as PCs, and then detects and analyzes behavior that suggests internal wrongdoing. The solutions will detect and analyze risks of internal impropriety that could lead to information leaks. These solutions will be made available and represent Dtex Systems' first collaboration in Japan.
Going forward, Fujitsu will continue to contribute to the creation of a networked society in which everyone can feel safe and at ease, and will support the business continuity of customers by further strengthening its Global Managed Security Service using cutting-edge security technology.
Background
The Cybersecurity Management Guidelines(3), published by Japan's Ministry for Economy, Trade and Industry and the Information-technology Promotion Agency (IPA), call for companies to take such steps as preparing an emergency response system if one is the victim of a cyberattack, and preparing a system for rapid disclosure after damage has been discovered. When subjected to a targeted cyberattack, it is important to prevent the damage from spreading by taking rapid initial countermeasures such as identifying where the attack has penetrated and removing attacked devices from the network, but identifying the extent of an attack on an intranet requires advanced technology and several weeks, making it difficult to rapidly determine attack status and disclose it.
In addition, intentional internal wrongdoing by someone related to an organization is one of the main causes of information leaks, alongside targeted cyberattacks, and companies also face issues in discovering this type of activity.
In order to resolve these issues, Fujitsu is offering functionality that can rapidly identify the extent of damage from a targeted cyberattack, and is expanding its Global Managed Security Service to detect the risk of internal impropriety through its collaboration with Dtex Systems. This will work to strengthen security on the boundaries between the internet and an intranet, and also within intranets and endpoints.
http://www.acnnewswire.com/topimg/Low_FujitsuIntranetFig1.jpg
Figure 1: Strengthened areas of the Global Managed Security Service
New Functionality to Rapidly Identify the Extent of Damage
A proprietary high-speed forensic technology developed by Fujitsu Laboratories enables the rapid determination of the extent of damage from an attack by detecting and analyzing only behaviors unique to targeted attacks from internet communications data. With this new functionality, the Global Managed Security Service monitors a customer's intranet 24 hours a day, 365 days a year from the Security Operation Center(4). When an external intrusion from a targeted attack is detected, Fujitsu's security experts determine the extent of the damage in several tens of minutes, using the high-speed forensic technology developed by Fujitsu Laboratories, enabling rapid reporting to the customer.
With this functionality, customers can rapidly grasp the infection pathway used by the malware sent by the attacker, and which devices are infected. This means they can not only prevent the spread of the infection by removing only infected devices from the network, enabling early restoration of the attacked network environment, but they can also take immediate countermeasures aimed at business continuity, minimizing the damage.
http://www.acnnewswire.com/topimg/Low_FujitsuIntranetFig2.jpg
Figure 2: New functions utilizing high-speed forensic technology
About the Collaboration with Dtex Systems
Dtex Systems provides technology that collects metadata(5) of users' ordinary behavior in business, such as usage status and communications with outside parties, from endpoints such as PCs, and uses machine learning to understand the pattern of action in ordinary times. With this technology, it is possible to detect and notify supervisors of actions deviating from ordinary activity patterns.
Fujitsu is now set to collaborate with Dtex Systems in its first deal in Japan to offer solutions. Fujitsu's security experts will analyze the risks of internal impropriety leading to intentional information leaks and other potential harm, supporting rapid countermeasures by customers.
Comment from Christy Wyatt, CEO of Dtex Systems
"Insider incidents represent a majority of data breaches globally, which makes understanding user behavior critical to preventing data loss. We are thrilled to partner with Fujitsu, a trusted industry leader, to offer comprehensive and scalable security solutions that provide deep, contextual understanding of user behavior in Japan."
Sales Targets
Sales of security-related products and services of 300 billion yen per year in fiscal 2019.
(1) Forensic technology
Technology that collects and analyzes logs kept on electronic devices such as PCs, providing clear evidence of unauthorized access and information leaks.
(2) Endpoint
A computer or information device connected to a wireless network or network device.
(3) Cybersecurity Management Guidelines
A document incorporating three principles managers should recognize, and ten instructions they should give their Chief Information Security Officers (CISO), in order for companies to promote cybersecurity countermeasures under the leadership of management. This was first formulated in December of 2015, and revised in December 2016.
(4) Security Operation Center
An organization that monitors and analyzes logs, such as from security products, network devices, and servers, and detects and notifies customers of cyberattacks.
(5) Metadata
Data (information) that provides information about other data.
Contact:
Fujitsu Limited
Public and Investor Relations
Tel: +81-3-3215-5259
URL: www.fujitsu.com/global/news/contacts/
Topic: Press release summary
Source: Fujitsu Ltd
Sectors: Cloud & Enterprise, CyberSecurity
http://www.acnnewswire.com
From the Asia Corporate News Network
Copyright © 2024 ACN Newswire. All rights reserved. A division of Asia Corporate News Network.
|
|
|

|
|
|
|
| Fujitsu Ltd |
| Apr 23, 2024 09:25 HKT/SGT |
|
Fujitsu SX Survey reveals key success factors for sustainability |
| Apr 22, 2024 15:09 HKT/SGT |
|
Fujitsu and METRON collaborate to drive ESG success: slashing energy costs, boosting productivity with new manufacturing industry solutions |
| Apr 19, 2024 09:17 HKT/SGT |
|
Fujitsu develops technology to convert corporate digital identity credentials, enabling participation of non-European companies in European data spaces |
| Apr 18, 2024 10:14 HKT/SGT |
|
Fujitsu and Oracle collaborate to deliver sovereign cloud and AI capabilities in Japan |
| Apr 11, 2024 14:10 HKT/SGT |
|
DOCOMO, NTT, NEC and Fujitsu Develop Top-level Sub-terahertz 6G Device Capable of Ultra-high-speed 100 Gbps Transmission |
| Apr 9, 2024 09:39 HKT/SGT |
|
Fujitsu AI transforms manufacturing lines with new quality control system for REHAU |
| Apr 1, 2024 15:17 HKT/SGT |
|
Fujitsu signs MoU with Mitsubishi UFJ Financial Group, Inc. to drive nature positive actions |
| Mar 29, 2024 09:28 HKT/SGT |
|
Fujitsu Selected as CDP Supplier Engagement Leader |
| Mar 26, 2024 09:24 HKT/SGT |
|
Fujitsu Tech Leverages AI and Underwater Drone Data for 'Ocean Digital Twin' |
| Mar 19, 2024 09:34 HKT/SGT |
|
Fujitsu Limited announces recruitment plans |
| More news >> |
 |
|
 |
|