- Over 50 million passwords stolen in 7 months of 2022
- Underground market value of stolen logs and compromised card details around US$5.8 million
- India saw the highest number of infected devices in the Asia Pacific, followed closely by Indonesia, Philippines and Vietnam
Singapore, Nov 29, 2022 - (ACN Newswire) - Group-IB, one of the global leaders in cybersecurity, has identified 34 Russian-speaking groups that are distributing info-stealing malware under the stealer-as-a-service model. The cybercriminals use mainly Racoon and Redlinestealers to obtain passwords for gaming accounts on Steam and Roblox, credentials for Amazon and PayPal, as well as users' payment records and crypto wallet credentials. In the first seven months of 2022, the gangs collectively infected over 890,000 user devices and stole over 50 mln passwords. All the identified groups orchestrate their attacks through Russian-language Telegram groups, although they mainly target users in the United States, Brazil, India, Germany, and Indonesia. In 2022, info-stealing malware has grown into one of the most serious digitalthreats.
Classiscam graduates
By tracking the evolution of the popular scam scheme Classiscam, Group-IB Digital Risk Protection analysts revealed how some "workers" (low-rank online scammers) started shifting to a more dangerous criminal scheme that involves distributing info stealers. Moreover, the illicit business of stealers, which is coordinated via Telegram groups, uses exactly the same operational model as Classiscam
An info stealer is a type of malware that collects credentials stored in browsers (including gaming accounts, email services, and social media), bank card details, and crypto wallet information from infected computers, and then sends all this data to the malware operator. After a successful attack, the scammers either obtain money themselves using the stolen data, or they sell the stolen information in the cybercriminal underground. According to Group-IB, stealers are one of the top threats to watch in the coming year. The threat actor responsible for the most recent attack on Uberpurchased the credentials compromised with the Racoon stealer.
According to the Group-IB Digital Risk Protection team, (part of the Unified Risk Platform), the mass Telegram groups and bots designed to distribute info stealers first appeared in early 2021. By investigating a number of accounts, Group-IB analysts were able to confirm that members of several scam groups that previously participated in the Classiscam scheme began using stealers. In 2021 and 2022, Group-IB experts identified 34 active groups on Telegram. On average, such info stealer distribution groups have around 200 active members.
The most popular stealer among the groups examined by Group-IB is RedLine, which is used by 23 out of 34 gangs. Racoon ranks second: 8 groups employ this tool. Custom stealers are used in 3 communities. Administrators usually give workers both RedLine and Racoon in exchange for a share of the stolen data or money. However, the malware in question is offered for rent on the dark web for $150-200 per month. Some groups use 3 stealers at the same time, while others have only one stealer in their arsenal.
Having switched from scamming users of classified websites to stealers, some threat actors reproduced not only the hierarchy and model of Classiscam, but also its technical capabilities. In particular, Telegram bots that generate malicious content, communication between members, and all their shady accounting. The tasks of workers, the scammers of the lower-ranks, have also changed — they must now drive traffic to bait scam websites impersonating well-known companies and convince victims to download malicious files. Cybercriminals embed links for downloading stealers into video reviews of popular games on YouTube, into mining software or NFT files on specialized forums and direct communication with NFT artists, and into lucky draws and lotteries on social media.
Telegram Stealers world tour
Group-IB estimates that between March 1 (when Group-IB started researching the scheme) and December 31, 2021 stealers operated via Telegram groups were able to compromise 538,000 devices. In the first 7 months of 2022, Telegram stealers were found to be almost twice more active infecting more than 890,000 devices in 111 countries.
The top 5 most often attacked countries in 2022 were the United States, Brazil, India, Germany, and Indonesia with 91,565, 86,043, 53,988, 40,750, and 35,345 infected devices respectively.
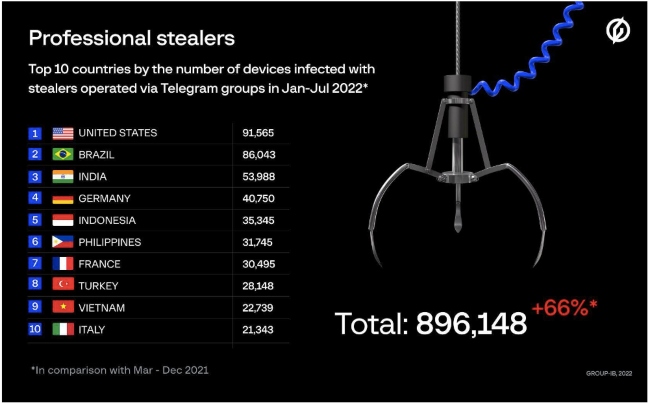
List of countries in Asia Pacific by the number of infected devices include India, Indonesia, Philippines, Vietnam and Singapore. In India for example, from March - December 2021, the operators of the stealers in question infected 19,249 devices. In the first seven months of 2022, the number grew to 53,988. Scammers were able to retrieve 4,547,020 passwords, 4,657 sets of payment records, and 4,428 sets of crypto wallet information such as credentials, seed phrases, etc.
Indonesia closely follows with a total of 35,345 infected devices and where scammers were able to retrieve 2,372,893 passwords. The Philippines recorded a total of 31, 745 infected devices and Vietnam with a total of 22,739 devices infected and scammers retrieving 2,032,278 passwords. Australia had 5,794 devices infected and 549,640 passwords retrieved by scammers. Singapore saw 2,179 devices infected, with 185,689 passwords retrieved.
According to the analysis of Telegram groups, for the last 10 months of 2021 cybercriminals collected 27,875,879 sets of passwords, 1,215,532,572 cookie files, 56,779 sets of payment records, and data from 35,791 crypto wallets. In the first 7 months of 2022, threat actors stole 50,352,518 passwords, 2,117,626,523 cookie files, details of 103,150 bank cards, and data from 113,204 crypto wallets. The underground market value of just the stolen logs and compromised card details is around $5.8 million, Group-IB experts estimate.

According to Group-IB, in 2021, threat actors worldwide most frequently collected PayPal account credentials (more than 25%) and Amazon credentials (more than 18%). In 2022, the most targeted services are the same, namely PayPal (more than 16%) and Amazon (more than 13%). However, over the course of the year, cases of stealing passwords for gaming services (Steam, EpicGames, Roblox) in the logs have increased almost five-fold.
"The influx of a huge number of workers into the popular scam Classiscam — which Group-IB's Unified Risk Platformidentified, at its peak, comprised over a thousand criminal groups and hundreds of thousands of fake websites — has led to criminals competing for resources and looking for new ways to make profits," says Ilia Rozhnov, head of Group-IB's Digital Risk Protection in the Asia Pacific. "The popularity of schemes involving stealers can be explained by the low entry barrier. Beginners do not need to have advanced technical knowledge as the process is fully automated and the worker's only task is to create a file with a stealer in the Telegram bot and drive traffic to it. For victims whose computers become infected with a stealer, however, the consequences can be disastrous."
To minimize potential risks, Group-IB Digital Risk Protection experts recommend that users refrain from downloading software from suspicious sources, use isolated virtual machines or alternative operating systems for installation, avoid saving passwords in browsers, and regularly clear browser cookies. To prevent digital risks and unwanted consequences, companies should take a proactive approach to their brand's digital security and use modern technologies for monitoring and response, such as Group-IB's Digital Risk Protection.
About Group-IB
Group-IB, with its headquarters in Singapore, is one of the leading solutions providers dedicated to detecting and preventing cyberattacks, identifying online fraud, investigating high-tech crimes, and protecting intellectual property. The company's Threat Intelligence and Research Centers are located in the Middle East (Dubai), Asia-Pacific (Singapore), and Europe (Amsterdam).
Group-IB's Unified Risk Platform is an ecosystem of solutions that understands each organization's threat profile and tailors defenses against them in real time from a single interface. The Unified Risk Platform provides complete coverage of the cyber response chain. Group-IB's products and services consolidated in Group-IB's Unified Risk Platform include Group-IB's Threat Intelligence, Managed XDR, Digital Risk Protection, Fraud Protection, Attack, Surface Management, Business Email Protection, Audit & Consulting, Education & Training, Digital Forensics & Incident Response, Managed Detection & Response, and Cyber Investigations. Group-IB's Threat Intelligence system has been named one of the best in its class by Gartner, Forrester, and IDC. Group-IB's Managed XDR, intended for proactively searching for and protecting against complex and previously unknown cyber threats, has been recognized as one of the market leaders in the Network Detection and Response category by KuppingerCole Analysts AG, the leading European analyst agency, while Group-IB itself has been recognized as a Product Leader and an Innovation Leader. Gartner has named Group-IB a Representative Vendor in Online Fraud Detection for its Fraud Protection. In addition, Group-IB was granted Frost & Sullivan's Innovation Excellence award for Digital Risk Protection (DRP), an Al-driven platform for identifying and mitigating digital risks and counteracting brand impersonation attacks, with the company's patented technologies at its core. Group-IB's technological leadership and R&D capabilities are built on the company's 19 years of hands-on experience in cybercrime investigations worldwide and over 70,000 hours of cybersecurity incident response accumulated in our leading DFIR Laboratory, High-Tech Crime Investigations Department, and round-the-clock CERT-GIB.
Group-IB is an active partner in global investigations led by international law enforcement organizations such as Europol and INTERPOL. Group-IB is also a member of the Europol European Cybercrime Centre's (EC3) Advisory Group on Internet Security, which was created to foster closer cooperation between Europol and its leading non-law enforcement partners.
Group-IB's experience in threat hunting and cyber intelligence has been fused into an ecosystem of highly sophisticated software and hardware solutions designed to monitor, identify, and prevent cyberattacks. Group-IB's mission is to protect its clients in cyberspace every day by creating and leveraging innovative solutions and services.
For more information, please contact:
pr@group-ib.com
+65 3159-3798
https://www.group-ib.com
https://www.group-ib.com/blog
Twitter | LinkedIn |Facebook |Instagram |Telegram
Topic: Press release summary
Source: Group-IB
Sectors: Enterprise IT, CyberSecurity
http://www.acnnewswire.com
From the Asia Corporate News Network
Copyright © 2025 ACN Newswire. All rights reserved. A division of Asia Corporate News Network.
|